Data breaches are unfortunately inevitable, and traditional network security alone is no longer enough. Organizations need to change their focus from perimeter defenses to a data-centered approach. This keeps sensitive information protected no matter where it goes.
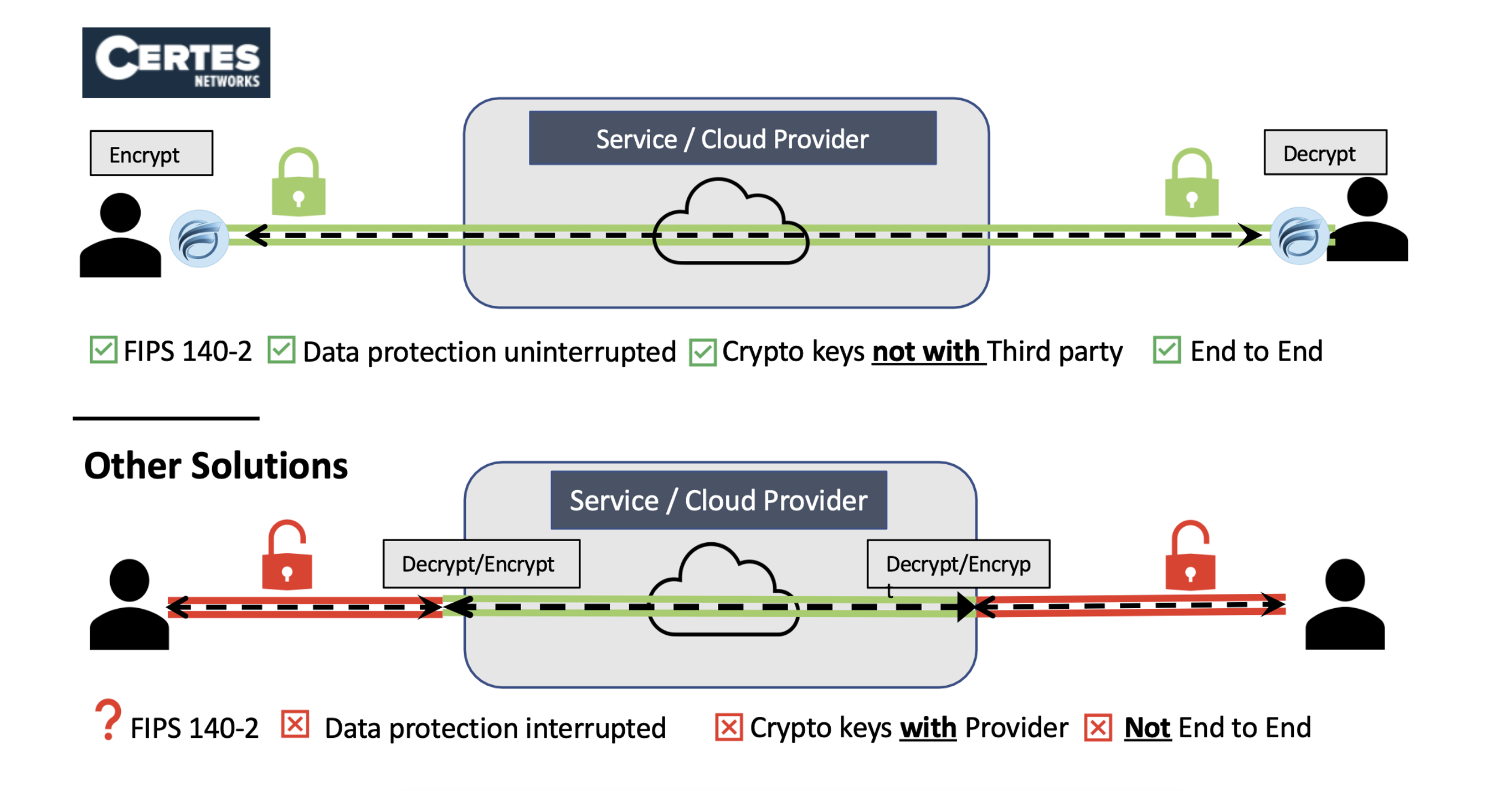
End-to-end encryption (E2EE) is essential for keeping data safe. It protects data before sending, while traveling, and during storage.
With rising regulatory demands and sophisticated cyber threats, businesses must act now to safeguard their most valuable asset: data.

What is End-to-End Encryption?
End-to-end encryption (E2EE) protects data from the moment someone creates it until it reaches the right person. Unlike traditional encryption methods that protect data only in certain states, E2EE keeps data encrypted all the time. This prevents unauthorized individuals from reading it.
How End-to-End Encryption works:
- Data is encrypted at the source before it leaves a device or system.
- It remains encrypted as it moves through networks, cloud environments, or storage systems.
- Only the intended recipient with the decryption key can access and read the data.
- Without the right decryption keys, stolen data is useless to cybercriminals. This is true even if they get past network security. This makes E2EE a critical defense against data breaches, ransomware attacks, and insider threats.
Why Businesses Need Data Encryption
Data is the primary target of cybercriminals. Businesses must protect sensitive data, like financial records, customer information, and trade secrets. This includes intellectual property. Here’s why encryption is non-negotiable:
- The Growing Threat of Cyberattacks
Cyberattacks have evolved beyond brute-force hacking. Attackers exploit stolen credentials, phishing schemes, and advanced malware to infiltrate systems undetected. Traditional security models that rely solely on firewalls and endpoint protection are no longer sufficient. Encryption ensures that even if unauthorized access occurs, the data remains unreadable and unusable.
- Regulatory Compliance & Industry Standards
Governments and regulatory bodies worldwide impose strict data protection requirements. Laws including GDPR, DORA, NIS2, and HIPAA require encrypting sensitive data. This helps prevent breaches and ensures compliance. Organizations that fail to implement adequate security measures face hefty fines and damage to their reputations.
- Protection Against Insider Threats
While external threats dominate cybersecurity headlines, insider threats, whether intentional or accidental, pose just as much risk. Employees, contractors, or partners with access to critical systems can compromise data security. E2EE mitigates these risks by ensuring that only authorized users with the correct decryption keys can access sensitive information.
How Certes Secures Data
Certes delivers advanced encryption and security solutions designed to protect data at every stage. By implementing a Zero Trust approach and ensuring faultless encryption, Certes empowers businesses to mitigate cyber risks effectively.
Encryption at the Source
Certes’ solutions encrypt data before it ever leaves its source device or application. This prevents unauthorized access from the outset and keeps sensitive information protected throughout its journey across networks.
Preventing Data Interception
Traditional security measures focus on protecting the perimeter, but attackers often gain access through stolen credentials or unpatched vulnerabilities. Certes ensures that even if an intruder breaches a system, the encrypted data remains unreadable and unusable.
Implementing Secure Data Practices
Businesses must take a proactive approach to cybersecurity by implementing secure data protection strategies. Here are key steps organizations can take:
- Adopt End-to-End Encryption – Encrypt data from creation to consumption to prevent unauthorized access.
- Implement Zero Trust Architecture – Assume that no user or device is trustworthy by default, requiring continuous verification.
- Regularly Rotate Encryption Keys – Reduce the risk of key compromise by frequently updating encryption keys.
- Secure Backups with Encryption – Protect backup data to prevent ransomware attacks from rendering recovery efforts useless.
- Train Employees on Cybersecurity Best Practices – Teach staff to spot and avoid cyber threats. This will help reduce human error.
Future Trends in Encryption
Cybersecurity threats are constantly evolving, and encryption technologies must adapt to stay ahead. Here’s what businesses should expect in the coming years:
- Quantum-Safe Encryption – As quantum computing advances, traditional encryption algorithms will become obsolete. Businesses must prepare for post-quantum cryptography to ensure future-proof security.
- AI-Driven Encryption – Artificial intelligence and machine learning will improve encryption methods. This will allow security measures to adapt to real-time threats.
- Enhanced Regulatory Requirements – Governments will continue tightening data protection laws, requiring businesses to adopt stronger encryption measures to remain compliant.
Learn More About Certes Solutions
Certes offers advanced encryption solutions. These help businesses protect sensitive data, stay compliant, and defend against new cyber threats. To improve network security, consider using a Zero Trust strategy.
If you want to protect your backups, Certes has the tools and knowledge to help. They can keep your organization safe. Request a Demo to learn how Certes can help you implement end-to-end encryption for ultimate data protection.

